The often-used analogy of a moat to protect company networks no longer applies. Because it must actually become more porous to work properly. Particularly flexible work and Cloud technologies require a new security approach.
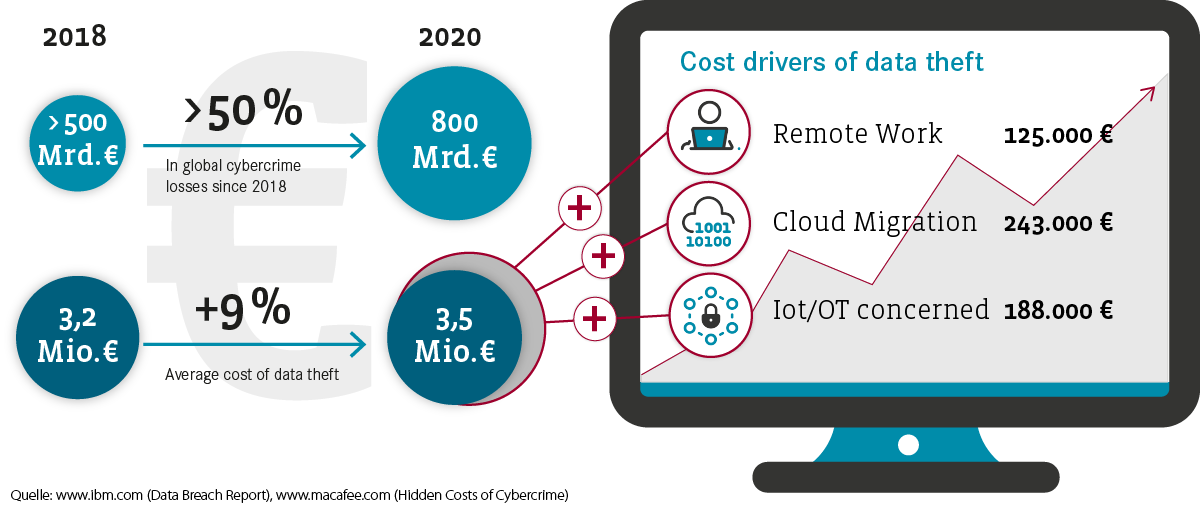
The Cloud and Remote Work are both a blessing and a curse. While the Digital Workplace increases productivity, promotes work-life balance and reduces costs in the era of COVID-19, it also has an enormous impact on the IT organization (especially with regard to security), and the resulting risks to the company are still unknown in many cases. The introduction of Zero Trust as a security concept makes it possible to actively address and minimize these risks. At the same time, it is important to be mindful of several challenges and traps that can arise during this process.
Tearing down walls
Virtually everyone and every company is afraid of break-ins. Closing windows, locking doors and building a wall around the business premises. This tactic has also been used in IT for a long time - in the form of perimeter protection for networks, which secures the company's resources. But these walls now have to become more porous so the company can utilize the advantages and opportunities offered by the Cloud and the workplace of the future. That is why companies must be in a position where access can be assessed and classified at all times. For example, how should one handle a situation where someone accesses sensitive company data in the ERP system from a public WiFi in a café? Is it a legitimate access by an employee or a clever cyber attack involving identity theft, with the potential of millions in damages?
Added to the above is the growing level of complexity due to IoT, BYOD, shadow IT, hybrid and multi Cloud. Today, more and more different devices are connected to the company's network or applications from more and more locations. At the same time, the enemy is learning ever faster and knows how to take advantage of this situation. Methods of attack are continuously enhanced and become more cost-effective. It is becoming easier for cyber criminals to create enormous damages. And there is another aspect that is often under-estimated: Even the strongest moat and strictest access controls do not protect against perpetrators on the inside.
Zero Trust as the solution
In such situations, there is only way to guarantee a high degree of security: Trust no one! This applies to users and devices equally. Because the laptop or smartphone of an innocent employee may contain malware. Similarly, IoT devices often lack security or cannot easily be protected with conventional means. The solution - consistent application of the Zero Trust concept.
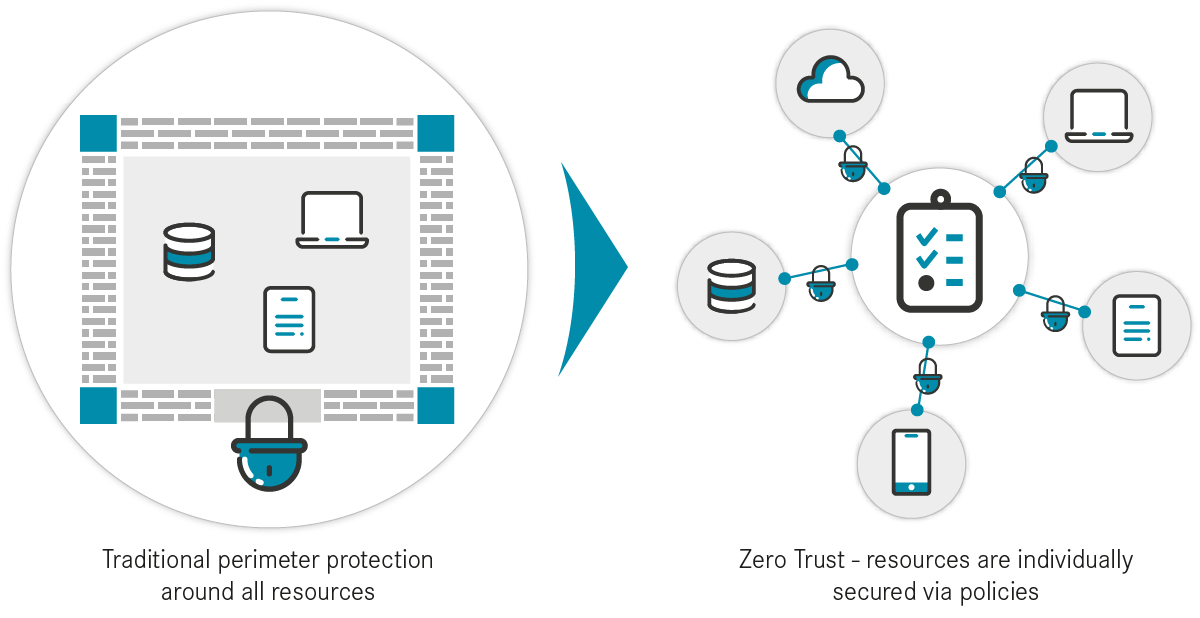
But how does it work? First, we have to accept that a security incident will happen sooner or later; it is something that cannot be avoided. Rather, the objective is to raise the cost of mounting a cyber attack while also minimizing the risk of damages. Instead of building a moat around the company's network, the network is divided into many small sections, each with its own security measures (see Figure 1). It is similar to a high-security facility with isolated rooms, each of which has its own biometric scanner, permanent camera monitoring and other security measures.
Instead of using a comprehensive but porous line of protection, resources are protected individually. Even though the Zero Trust concept has been discussed as far back as 2003, it has only recently become accessible to most companies due to new and cost-effective products. This encourages the democratization of high-security products in IT.
The virtual doorman
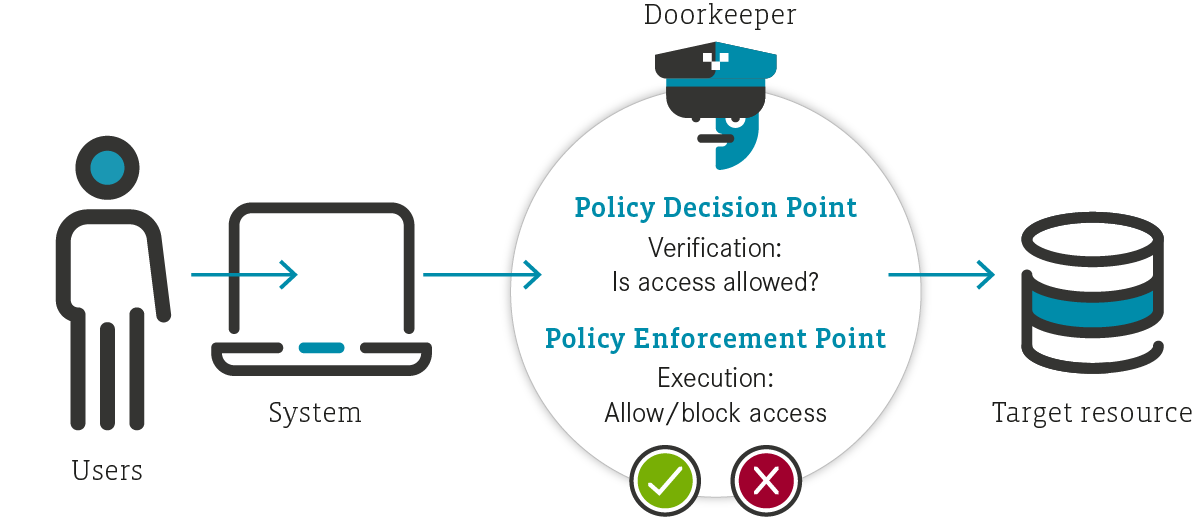
At the heart of the Zero Trust approach is a team of virtual doormen, which examines every guest and checks their access authorization. This “Policy Decision and Enforcement Point” then decides which of the company's resources can be accessed by the users and their devices. In the end, the concept is similar to having two doormen: One checks and decides (using pre-defined rules) whether the employee is allowed to access, while the second authorizes the access (or not) (see Figure 2).
What this means: While previously employees only had to enter their password once a day and were then able to access everything, now every single access is checked in its relevant context.
This applies regardless of where the accessing person is located, or whether the target system is located in the company's data center or in the Cloud. In this context, the principle “never trust, always verify” is applied in combination with a Least Privilege Access approach. The latter provides each user and device with only those access rights that are required for the respective role and task.
Take, for example, someone accessing the ERP system from a café at night:
Individual protection = More security
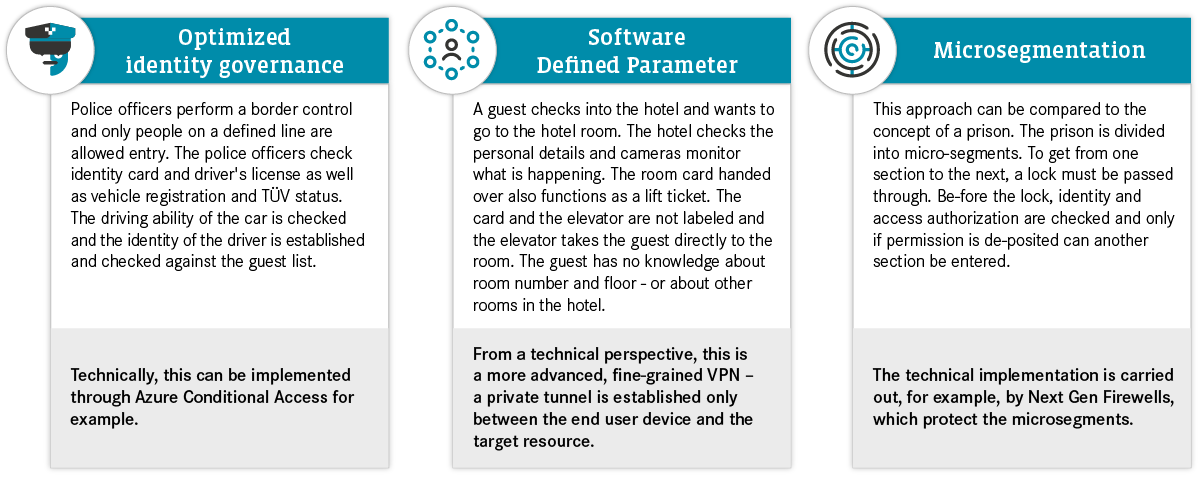
Zero Trust is a concept that companies use to continuously optimize their security. There are a variety of approach that can be used for this purpose; their application will depend on the company context (see Figure 3). The approaches differ in terms of complexity and cost, whereby optimized identity governance is the simplest approach for most companies, relatively speaking.
But what is the best way to introduce Zero Trust? The implementation of many remote work and Cloud initiatives is accelerated due to the COVID-19 crisis, but the necessary security aspects are neglected. To achieve success quickly and reduce the accumulated security aspects, the first step focuses on the Digital Workplace and the identity-based approach. Here, Zero Trust ensures the integrity of the identities and devices, and follows the Least Privilege Access approach. This includes integrating the devices into the IAM (Identity and Access Management) system, and the introduction of multi-factor authentication, at minimum for the Admin accounts. This does not require complex rebuilds in the network.
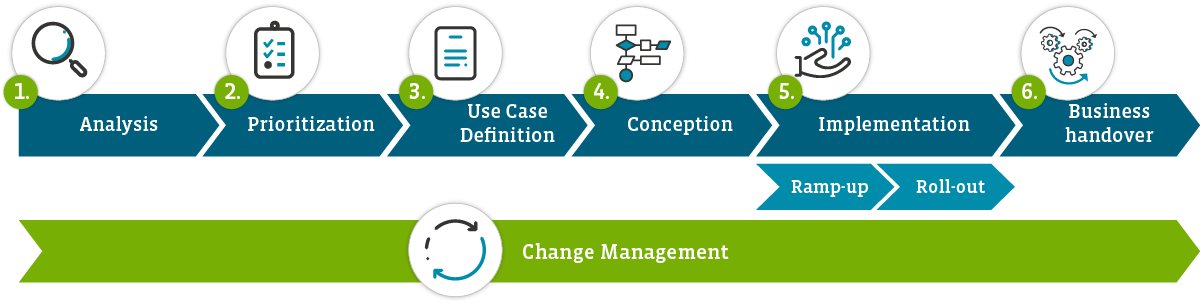
An integrated Zero Trust approach should be introduced at the same time. The following six steps are recommended:
Conclusion
Cloud, remote work, IoT and other trends turn the moat around the company's network into the equivalent of Swiss cheese. Comprehensive protection against ever more sophisticated IT attacks in an increasingly connected world requires immediate action. New and cost-effective products mean that such measures are now affordable for all companies. At the same time, the Zero Trust concept must be anchored in the IT strategy as a sort of IT Security concept, it must be promoted from the top down, and it must be accompanied by change management.